TREND MICRO SERVERPROTECT FOR LINUX DOWNLOAD FREE
System log on page , for an example of the system log. Register ServerProtect to ensure that you are eligible to receive the latest security updates and other product and maintenance services. Copy the new file to your ServerProtect remote. Copy the KHM to its corresponding directory on the deploying server. Backing Up and Verifying the Configuration File Whenever you make a change to ServerProtect for Linux configuration, Trend Micro recommends that you make a backup copy of the configuration file. SmtpTo This key contains the notification recipients. ServerProtect even gives you the option to specify your Internet-based update server. 
| Uploader: | Jujind |
| Date Added: | 13 July 2005 |
| File Size: | 33.41 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 21969 |
| Price: | Free* [*Free Regsitration Required] |
The Manual Update screen appears. Executing a manual scan does not require running or triggering serveprotect KHM. There is no default password. In response to customer requests, this limit is now configurable by editing the tmsplx.
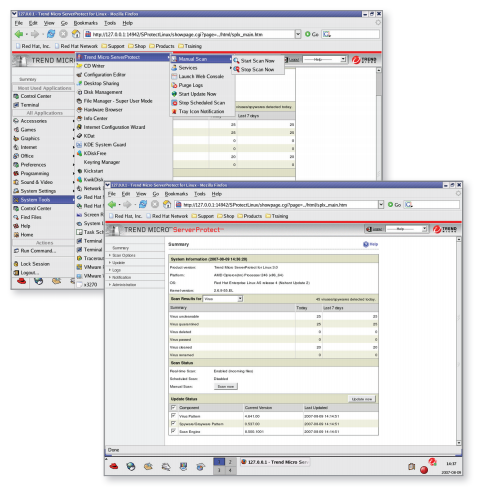
Note that the Gnome desktop environment is not supported. VirusOutbreakPeriod This key sets the time interval, in minutes, between virus outbreak notifications. The Stored Logs section of the screen displays the number of logs currently in the log database, and the date range of the stored logs, if any. Registration Group Serverrotect The keys in this group contain data used by ServerProtect for product registration and activation.
Trend Micro - Anti-virus
Using a text editor such as vi, edit the following configuration files: Here is an example of an Activation Code: This section describes how to install the kernel hook module KHM for your server if you are not using the default kernels provided during installation of ServerProtect for Linux or if the KHM is updated after installation and you need to install a more current version of serverpgotect KHM. Specifying the Backup Directory Location ServerProtect can back up infected files before Real-time Scan, Scan Now, or Scheduled Scan performs the Clean action first, select the clean action for the desired scan type s.
If you are not a registered user, click Continue on the right side of the screen.
The installer stores your port number and asks if you use a proxy to connect to Control Manager. A Using splx Script Type the full path of the desired files, and then separate them with a colon: Due to the large number of new viruses, always keep the foe pattern file up-to-date.
MiTM and remote code vulnerabilities found in Trend Micro ServerProtect
Select Edit Runlevel on the menu and then choose level 3 to 5 to edit. Alternatively, copy the following characters into a text file, and then save the file with a com extension for example, virus. The uninstallation commands are different depending on which Linux distribution your system is using, as shown in the table below.
The daily order placement cut-off time to ensure credit card approval and delivery within expectations is 9: Hover your cursor over the tooltip icon for more explanation of this feature. Modify the default notifications by deleting the existing text and typing your new text in the Message fields.
To activate ServerProtect at the Product Registration screen: Trend Micro recommends testing the deployment on a small number of machines before executing a deployment to your entire network. An error occured while adding the item s to linud. Using the GUI only: The default value is 3. ServerProtect gives renamed files the extension "VIR.
how i can install Trend Micro ServerProtect - CentOS
To terminate these processes gracefully, use the -a option. Make the appropriate modifications, then click Save.

Please refer to the Intel Web site for more details on this technology. Please evaluate this documentation on the following site: However, you can change your password at a later time on this screen.
Trend Micro™ ServerProtect™ for Linux™ Getting Started Guide
Copy the KHM to its corresponding directory on the deploying lniux. Unlike threats such as viruses, worms, and Trojans, grayware does not infect, replicate, or destroy data, but it may violate your privacy. Schedule This key specifies the schedule for a scheduled update.

Комментарии
Отправить комментарий